
You can now move on to the overlay configuration.
In this section, you will create the necessary files to configure the VRFs and Networks for your fabric.
You will start by creating the vrfs.nac.yml file.
This file will contain the VRF configuration for your fabric, which defines the VRF names, VRF IDs, VLAN IDs, and VRF attach groups for attaching to switches.
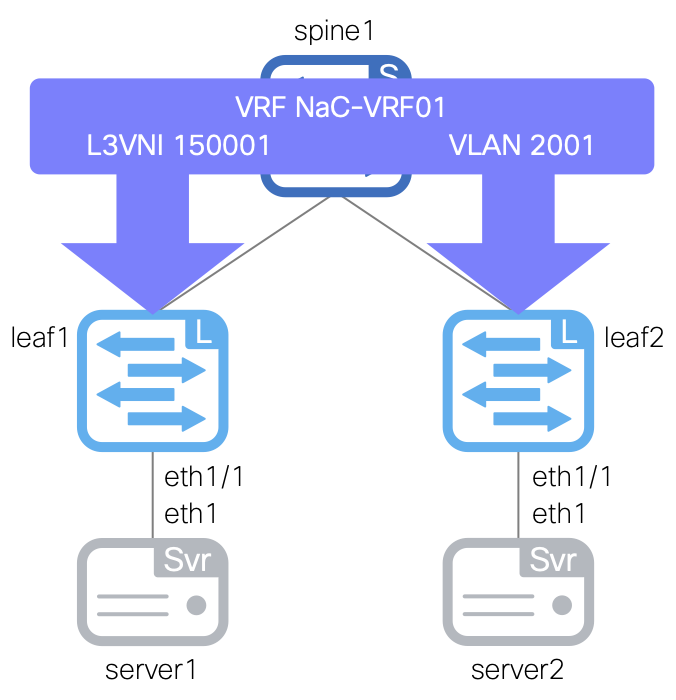
You will start by defining a single VRF named NaC-VRF01 with a VRF ID of 200001 and VLAN ID of 2001. This VRF will be attached starting with your vPC peers using the all VRF attach group which will later be used to pickup all switches in the fabric.
touch ~/workspace/ndlab/nac/host_vars/site1-fabric/vrfs.nac.yml
code-server -r ~/workspace/ndlab/nac/host_vars/site1-fabric/vrfs.nac.yml
---
vxlan:
overlay:
vrfs:
- name: NaC-VRF01
vrf_id: 200001
vlan_id: 2001
vrf_attach_group: all
vrf_attach_groups:
- name: all
switches:
- hostname: site1-l1
- hostname: site1-l2
Next, you will create the networks.nac.yml file.
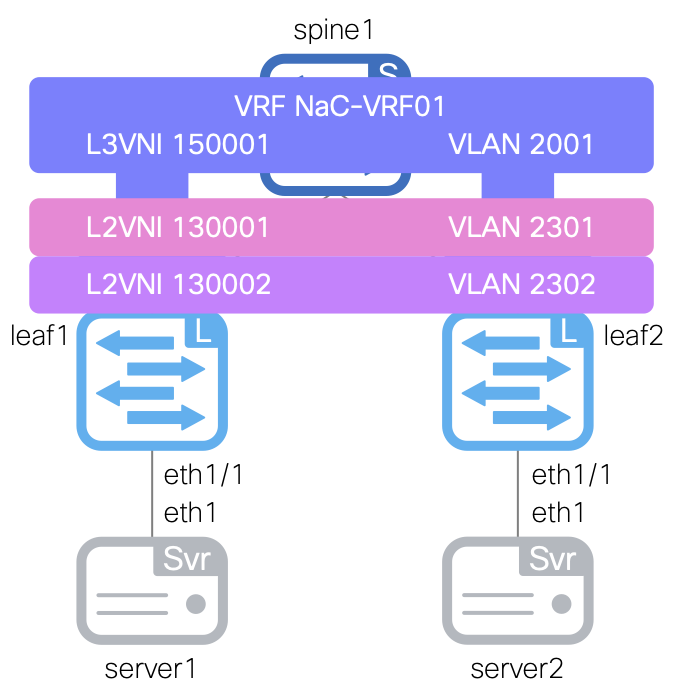
This file will contain the Network configuration for your fabric, which defines the network names, VRF names (newly created above), network IDs, VLAN IDs, VLAN names, gateway IP addresses, and network attach groups.
Your initial set of data will define two networks named NaC-Net01 and NaC-Net02 and both associated to the previously created VRF NaC-VRF01 and attached to your vPC peers. You will also define two network attach groups named leaf1_leaf2_access and leaf1_leaf2_vpc to attach the networks to the appropriate interfaces on your leaf switches based on access or vPC interfaces defined in the previous section. The access group will attach to ethernet1/4 on both leaf switches which will be access ports while the vPC group will attach to port-channel5 on both leaf switches which will be trunk ports.
touch ~/workspace/ndlab/nac/host_vars/site1-fabric/networks.nac.yml
code-server -r ~/workspace/ndlab/nac/host_vars/site1-fabric/networks.nac.yml
---
vxlan:
overlay:
networks:
- name: NaC-Net01
vrf_name: NaC-VRF01
net_id: 240001
vlan_id: 2401
vlan_name: NaC-Net01_vlan2401
gw_ip_address: 192.168.1.1/24
network_attach_group: leaf1_leaf2_access
- name: NaC-Net02
vrf_name: NaC-VRF01
net_id: 240002
vlan_id: 2402
vlan_name: NaC-Net02_vlan2402
gw_ip_address: 192.168.2.1/24
network_attach_group: leaf1_leaf2_vpc
network_attach_groups:
- name: leaf1_leaf2_access
switches:
- hostname: site1-l1
ports:
- ethernet1/4
- hostname: site1-l2
ports:
- ethernet1/4
- name: leaf1_leaf2_vpc
switches:
- hostname: site1-l1
ports:
- port-channel5
- hostname: site1-l2
ports:
- port-channel5
Make sure you are in your root Ansible directory
cd ~/workspace/ndlab/nac
From the root Ansible project directory execute the following command:
ansible-playbook -i hosts.site1.yml vxlan.yml --tags cr_manage_vrfs_networks
Upon a successful run of the playbook your output should look as follows:
<... SNIP ...> PLAY RECAP ************************************************************************************************************************************************************ site1-fabric : ok=236 changed=34 unreachable=0 failed=0 skipped=793 rescued=0 ignored=0 PLAYBOOK RECAP ******************************************************************************************************************************************************** Playbook run took 0 days, 0 hours, 1 minutes, 47 seconds TASKS RECAP *********************************************************************************************************************************************************** Tuesday 27 January 2026 03:36:27 +0000 (0:00:00.623) 0:01:47.138 ******* =============================================================================== cisco.nac_dc_vxlan.create : Manage Fabric Networks in Nexus Dashboard ------------------------------------------------------------------------------------------ 4.88s cisco.nac_dc_vxlan.create : Manage Fabric VRFs in Nexus Dashboard ---------------------------------------------------------------------------------------------- 4.35s cisco.nac_dc_vxlan.common : Get POAP Data From POAP Enabled Devices -------------------------------------------------------------------------------------------- 2.23s cisco.nac_dc_vxlan.common : Display Flag Values ---------------------------------------------------------------------------------------------------------------- 2.16s cisco.nac_dc_vxlan.connectivity_check : Get Cisco Nexus Dashboard Fabric Controller Version -------------------------------------------------------------------- 1.70s cisco.nac_dc_vxlan.common : Get Multisite Fabric Associations in Nexus Dashboard ------------------------------------------------------------------------------- 1.36s cisco.nac_dc_vxlan.create : Attach Loopbacks to VRFs in Nexus Dashboard ---------------------------------------------------------------------------------------- 1.33s cisco.nac_dc_vxlan.common : Build Fabric Creation Parameters From Template ------------------------------------------------------------------------------------- 1.00s cisco.nac_dc_vxlan.common : Retrieve NDFC Device Username and Password from Group Vars and update inv_config --------------------------------------------------- 0.93s cisco.nac_dc_vxlan.common : Build Policy List From Template ---------------------------------------------------------------------------------------------------- 0.89s cisco.nac_dc_vxlan.common : Retrieve NDFC Device Username and Password from Group Vars and update inv_config --------------------------------------------------- 0.89s cisco.nac_dc_vxlan.validate : Copy Service Model Data to Host -------------------------------------------------------------------------------------------------- 0.80s cisco.nac_dc_vxlan.connectivity_check : Verify Authorization to Nexus Dashboard -------------------------------------------------------------------------------- 0.78s cisco.nac_dc_vxlan.common : Build Fabric Switch Inventory List From Template ----------------------------------------------------------------------------------- 0.77s cisco.nac_dc_vxlan.common : Build underlay IP address allocation From Template --------------------------------------------------------------------------------- 0.77s cisco.nac_dc_vxlan.common : Build Networks Attach List From Template ------------------------------------------------------------------------------------------- 0.75s cisco.nac_dc_vxlan.common : Build vPC interface ---------------------------------------------------------------------------------------------------------------- 0.75s cisco.nac_dc_vxlan.common : Build Interface -------------------------------------------------------------------------------------------------------------------- 0.75s cisco.nac_dc_vxlan.common : Build sub_interface ---------------------------------------------------------------------------------------------------------------- 0.74s cisco.nac_dc_vxlan.common : Build Interface Po ----------------------------------------------------------------------------------------------------------------- 0.74s ROLES RECAP *********************************************************************************************************************************************************** Tuesday 27 January 2026 03:36:27 +0000 (0:00:00.628) 0:01:47.142 ******* =============================================================================== common ----------------------------------------------------------------- 74.48s create ----------------------------------------------------------------- 16.40s validate ---------------------------------------------------------------- 6.48s connectivity_check ------------------------------------------------------ 3.89s common_global ----------------------------------------------------------- 0.04s ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ total ----------------------------------------------------------------- 101.29s
Return to your ND browser where you should be sitting on the Interfaces tab
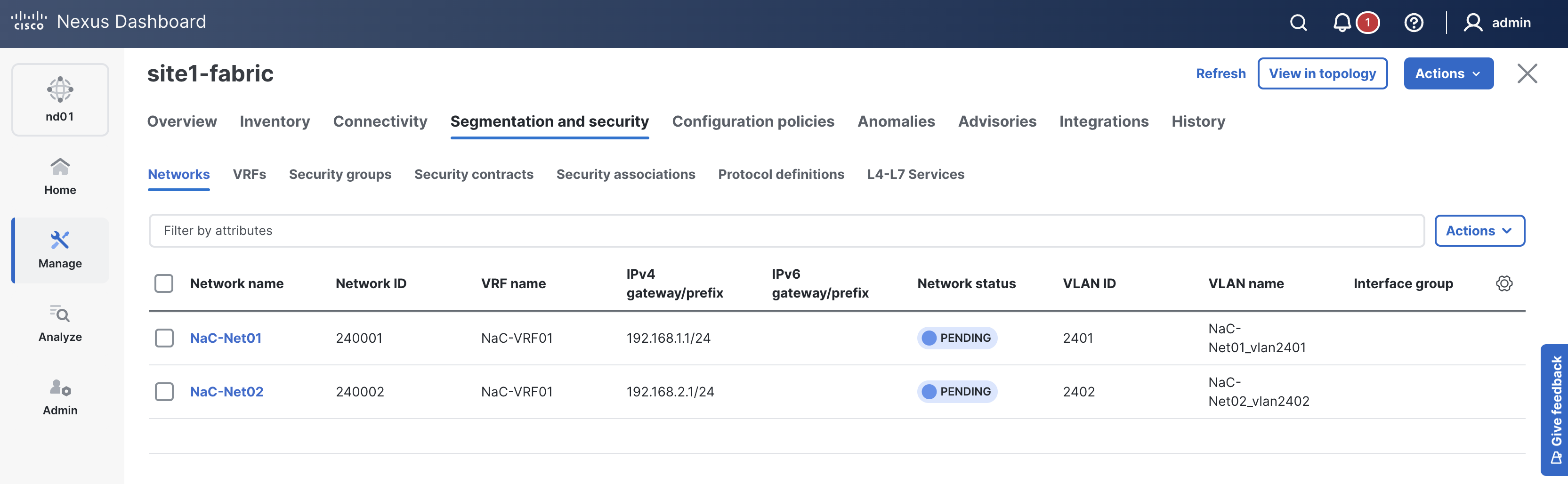
Verify you see the Networks NaC-Net01 and NaC-Net02 created.
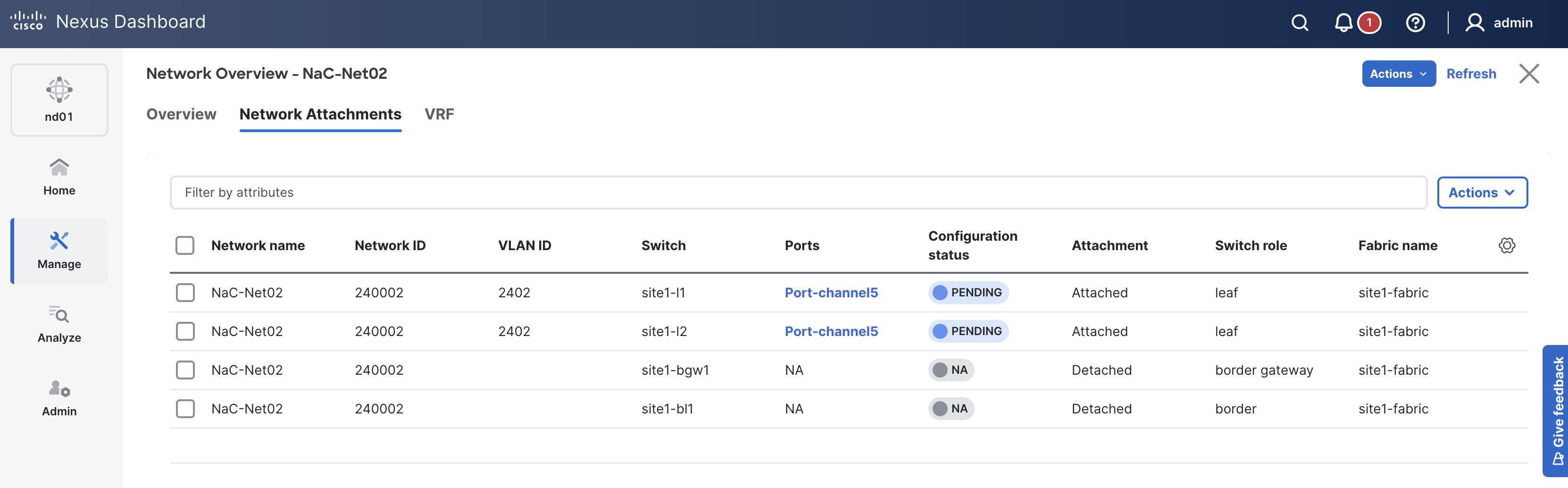
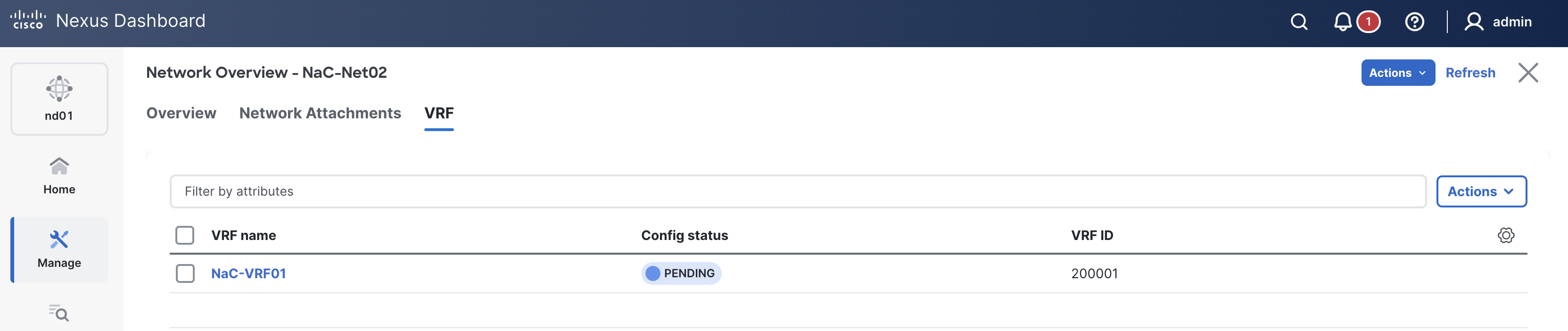
Verify you see the VRF NaC-VRF01 created.
Like previous sections, when reviewing the VRFs tab, it is expected to see VRFs in the Pending status since a deployment has not taken place yet. Again, you will deploy to your switches in the deploy role.
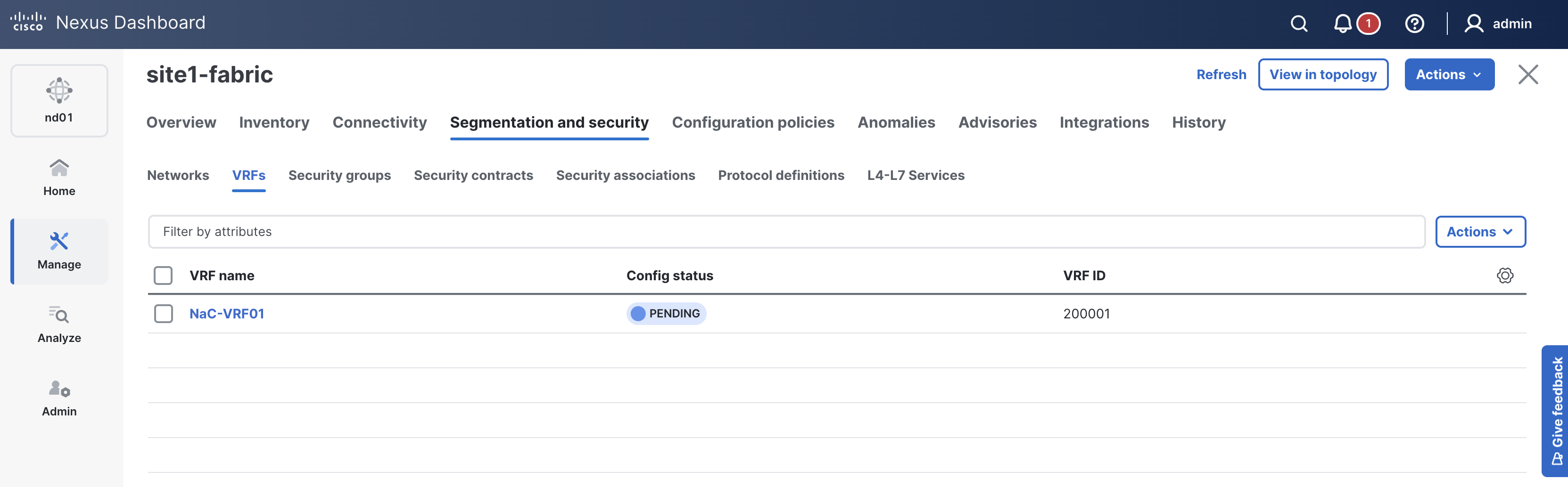
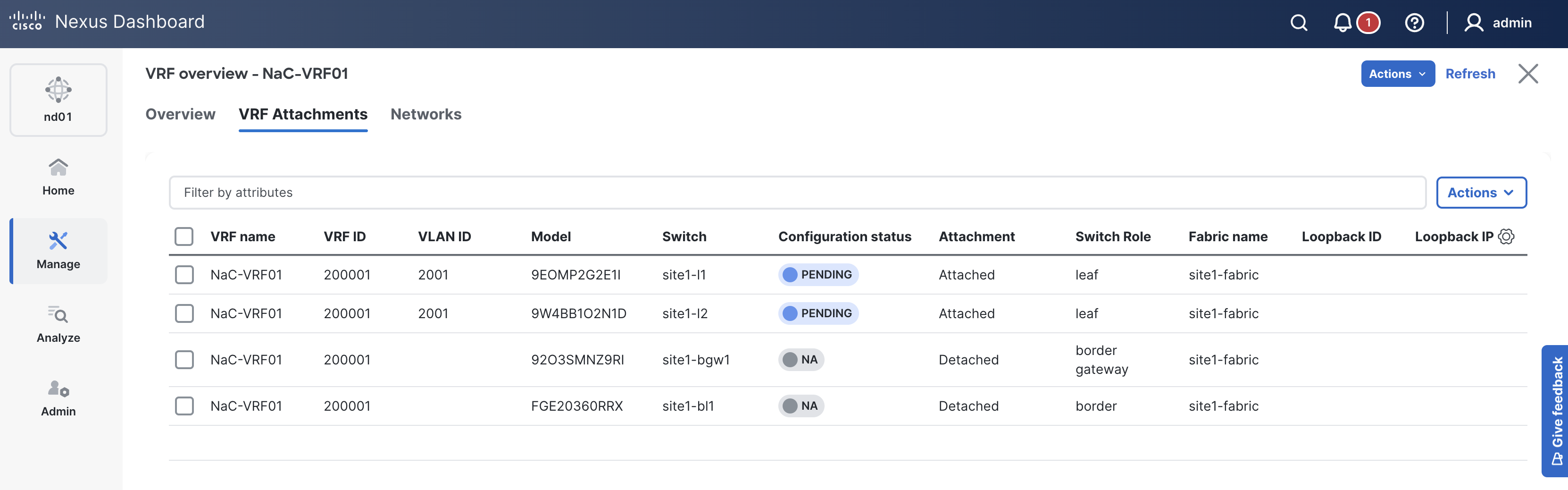
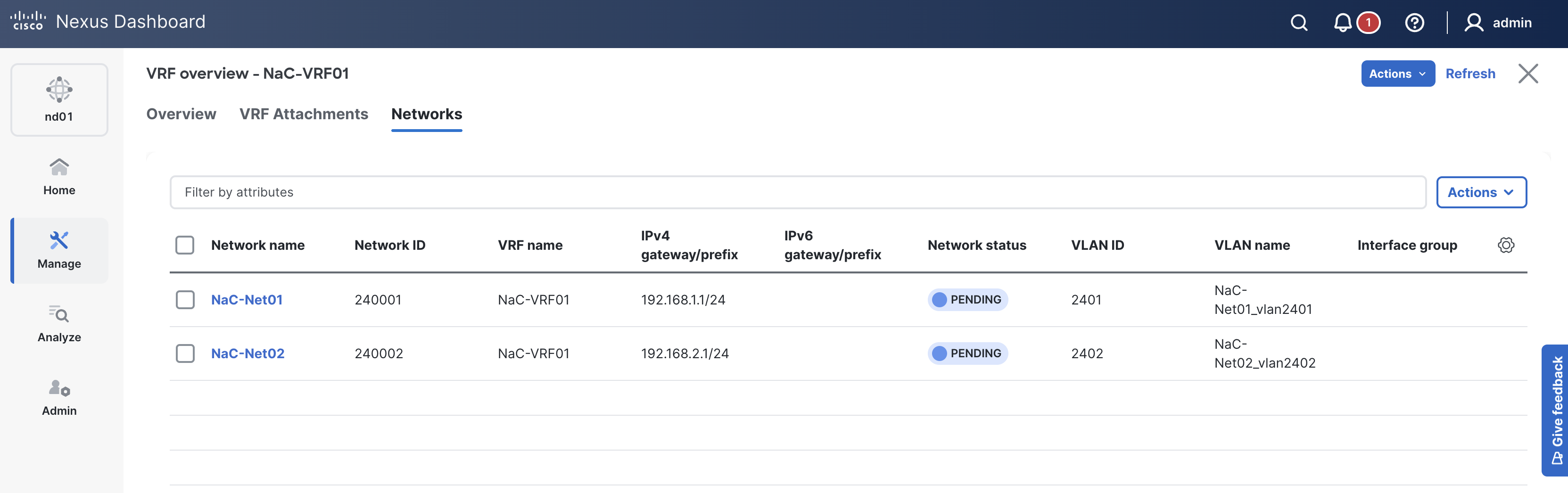
Navigate back to your VSCode application.
Continue to the next section to define different policies to augment the configuration that Nexus Dashboard provides.