
With the majority of the fabric configuration complete, you will now define some policies to be applied to all switches in your fabric.
You will start by creating the policy.nac.yml file, which defines policy templates, policy groups, and the assignment of those groups to switches in your fabric; even your pre-provisioned switches.
Policy can be defined in two different ways:
template_name and template_vars to reference pre-defined templates that ship with Nexus Dashboard.
filename to specify the path to a policy file. The filename can have two extensions: .cfg or .yml / .yaml.
.cfg, the file is treated as a freeform configuration file and the contents are pushed as-is.
.yml / .yaml, the file is treated as, and expected to be, a Nexus Dashboard template.
touch ~/workspace/ndlab/nac/host_vars/site1-fabric/policy.nac.yml
code-server -r ~/workspace/ndlab/nac/host_vars/site1-fabric/policy.nac.yml
---
vxlan:
policy:
policies:
- name: clock timezone
template_name: clock_timezone
template_vars:
TIME_ZONE: CET
HOUR_OFFSET: 1
MINUTE_OFFSET: 0
- name: clock summertime
template_name: clock_summertime
template_vars:
SUMMER_TIME: 'CEST 5 SUNDAY MARCH 02:00 5 SUNDAY OCTOBER 03:00 60'
- name: alias
template_name: switch_freeform
template_vars:
CONF: |-
cli alias name wr copy run start
- name: banner
template_name: banner
template_vars:
BANNER: |-
***************************************************************************
* Cisco Live - LTRDCN-3439 *
***************************************************************************
BANNERDELIMITER: "_"
TYPE: "motd"
groups:
- name: common policies
policies:
- name: clock summertime
- name: clock timezone
- name: alias
- name: banner
switches:
- name: site1-s1
groups:
- common policies
- name: site1-l1
groups:
- common policies
- name: site1-l2
groups:
- common policies
- name: site1-bl1
groups:
- common policies
- name: site1-bgw1
groups:
- common policies
Make sure you are in your root Ansible directory.
cd ~/workspace/ndlab/nac
From the root Ansible project directory execute the following command:
ansible-playbook -i hosts.site1.yml vxlan.yml --tags cr_manage_policy
Upon a successful run of the playbook your output should look as follows:
<... SNIP ...> PLAY RECAP ************************************************************************************************************************************************************ site1-fabric : ok=233 changed=33 unreachable=0 failed=0 skipped=736 rescued=0 ignored=0 PLAYBOOK RECAP ******************************************************************************************************************************************************** Playbook run took 0 days, 0 hours, 1 minutes, 37 seconds TASKS RECAP *********************************************************************************************************************************************************** Tuesday 27 January 2026 03:45:04 +0000 (0:00:00.568) 0:01:37.383 ******* =============================================================================== cisco.nac_dc_vxlan.create : Manage Fabric Policies in Nexus Dashboard ------------------------------------------------------------------------------------------ 2.86s cisco.nac_dc_vxlan.common : Get POAP Data From POAP Enabled Devices -------------------------------------------------------------------------------------------- 2.20s cisco.nac_dc_vxlan.common : Display Flag Values ---------------------------------------------------------------------------------------------------------------- 2.16s cisco.nac_dc_vxlan.connectivity_check : Get Cisco Nexus Dashboard Fabric Controller Version -------------------------------------------------------------------- 1.73s cisco.nac_dc_vxlan.common : Get Multisite Fabric Associations in Nexus Dashboard ------------------------------------------------------------------------------- 1.33s cisco.nac_dc_vxlan.common : Build Fabric Creation Parameters From Template ------------------------------------------------------------------------------------- 1.01s cisco.nac_dc_vxlan.common : Build Policy List From Template ---------------------------------------------------------------------------------------------------- 0.91s cisco.nac_dc_vxlan.common : Retrieve NDFC Device Username and Password from Group Vars and update inv_config --------------------------------------------------- 0.91s cisco.nac_dc_vxlan.common : Retrieve NDFC Device Username and Password from Group Vars and update inv_config --------------------------------------------------- 0.89s cisco.nac_dc_vxlan.validate : Copy Service Model Data to Host -------------------------------------------------------------------------------------------------- 0.81s cisco.nac_dc_vxlan.common : Build Fabric Switch Inventory List From Template ----------------------------------------------------------------------------------- 0.81s cisco.nac_dc_vxlan.connectivity_check : Verify Authorization to Nexus Dashboard -------------------------------------------------------------------------------- 0.79s cisco.nac_dc_vxlan.common : Build sub_interface ---------------------------------------------------------------------------------------------------------------- 0.78s cisco.nac_dc_vxlan.common : Build Interface -------------------------------------------------------------------------------------------------------------------- 0.76s cisco.nac_dc_vxlan.common : Build vPC interface ---------------------------------------------------------------------------------------------------------------- 0.75s cisco.nac_dc_vxlan.common : Build Interface -------------------------------------------------------------------------------------------------------------------- 0.75s cisco.nac_dc_vxlan.common : Build Interface -------------------------------------------------------------------------------------------------------------------- 0.74s cisco.nac_dc_vxlan.common : Build Networks Attach List From Template ------------------------------------------------------------------------------------------- 0.72s cisco.nac_dc_vxlan.common : Build VRFs Attach List From Template for loopback ---------------------------------------------------------------------------------- 0.72s cisco.nac_dc_vxlan.common : Build Interface -------------------------------------------------------------------------------------------------------------------- 0.72s ROLES RECAP *********************************************************************************************************************************************************** Tuesday 27 January 2026 03:45:04 +0000 (0:00:00.570) 0:01:37.385 ******* =============================================================================== common ----------------------------------------------------------------- 74.65s validate ---------------------------------------------------------------- 6.95s create ------------------------------------------------------------------ 5.85s connectivity_check ------------------------------------------------------ 3.94s common_global ----------------------------------------------------------- 0.05s ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ total ------------------------------------------------------------------ 91.44s
Return to your ND browser where you should be sitting on the Configuration policies tab
enter
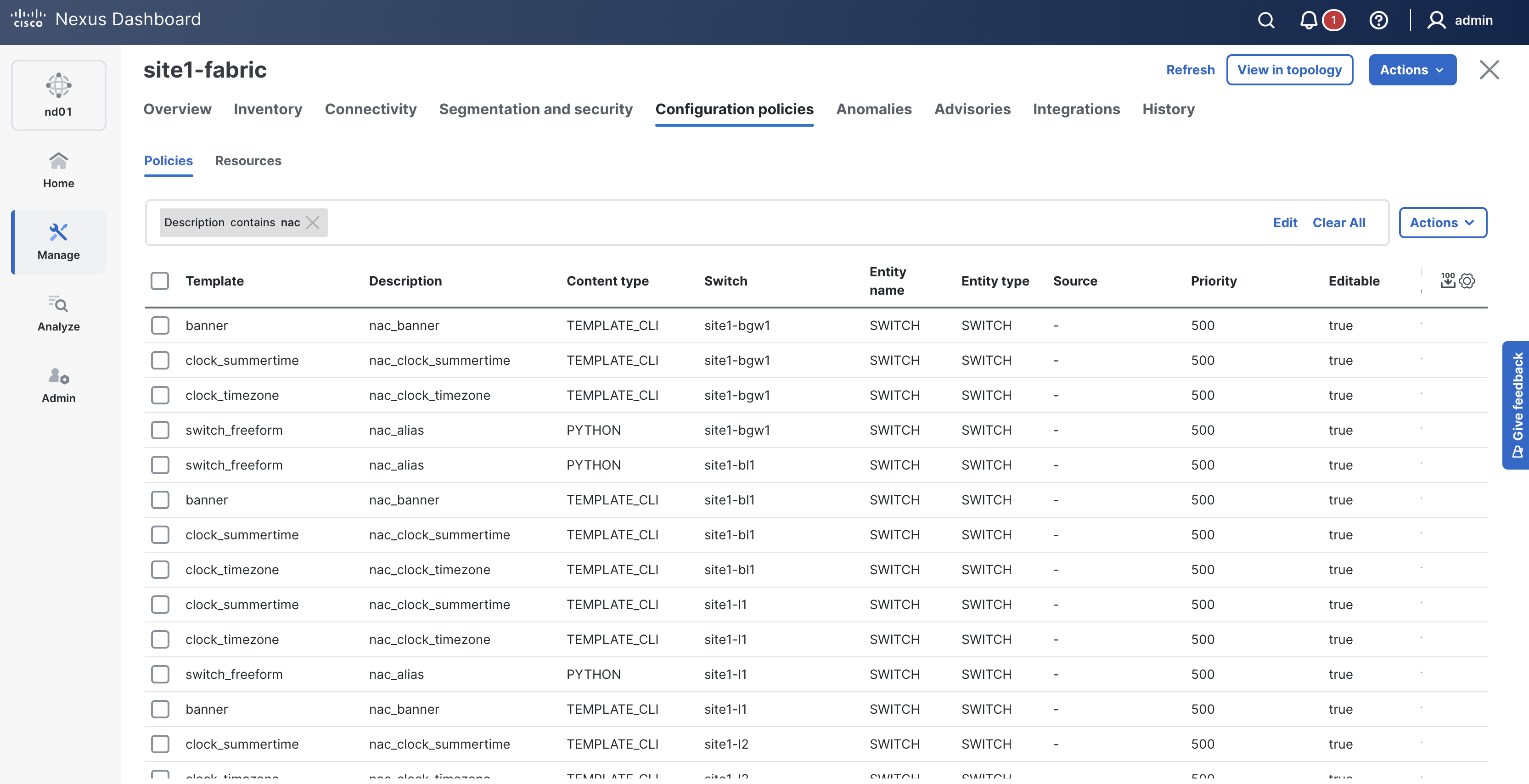
You will see the policies you declared in your policy.nac.yml file have been created in ND.
Network as Code prepends the string "nac" in the description of each policy it creates and manages.
Navigate back to your VSCode application.
Continue to the next section to deploy all of your staged configuration to your fabric.